Setting up Windows Defender Firewall for VPN kill switch
Background
Let’s say you are setting up a VPN client on Windows. And you want to ensure that all Internet traffic will go through the VPN tunnel. How to prevent leaking connections if the tunnel is going down? Going further, how to ensure that all software on the machine even using the tunnel?
This is the technique called kill switch. If VPN is not working - nothing is working, Internet (or even network in general) is not available. Some of VPN providers have it built-in into their client software. However, since the topic is a bit sensitive it needs some guarantees that nothing is bypassing the tunnel. Something really trustworthy and independent from all the variety of VPN vendors. Something like 🔥system firewall🔥.
Windows Defender Firewall Basics
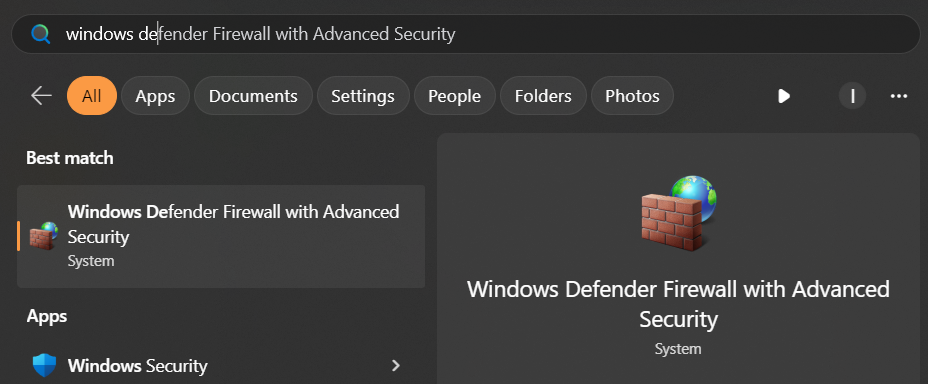
First of all, firewall needs to be enabled: open it, right-click the root node of the tree at the left and choose “Properties”.
Windows firewall defines 3 so-called profiles. Profile is a configuration applied to a specific type of the networks. There are 3 of them: Domain, Private and Public.
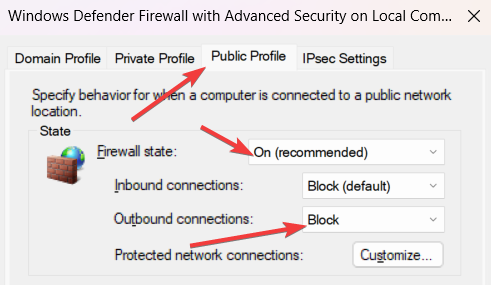
But what does it mean? A computer needs a network interface in order to connect to the network. For example, an Ethernet or WiFi adapter. But those are physical adapters. There is also a number of virtual network adapters created by software like VPN clients. Both physical and virtual adapters can be found in Control panel at Control Panel\Network and Internet\Network Connections.
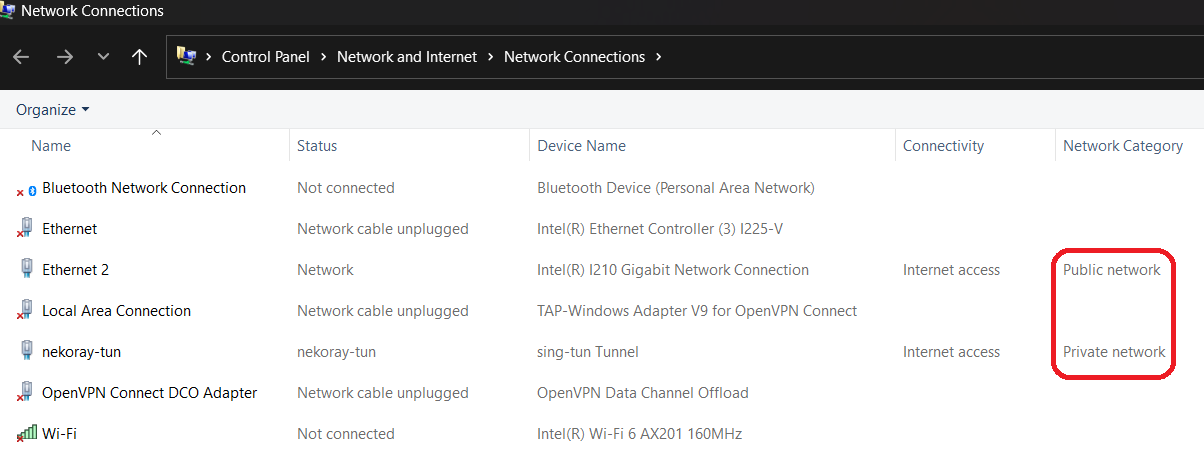
Pay attention to Network Category column. This is exactly the firewall profile applied to this connection.
Usually, Windows sets a new network connection Public by default. At that moment you can also see an annoying prompt which is confirming this choice. Now it finally makes sense and becomes really important.
Coming back to the firewall, all outbound connections should be disabled for Public and enabled for Private networks by default. All (physical) networks will become public and only VPN - private. In order to change network category/firewall profile for an adapter, next Powershell command should be run in elevated (as Admin) Powershell:
1Set-NetConnectionProfile -InterfaceAlias "Local Area Connection" -NetworkCategory "Private"
At this point, we have firewall enabled and outbound connections blocked by default for Public networks. However, this is just the default rule. There are also numerous specific rules set by software.
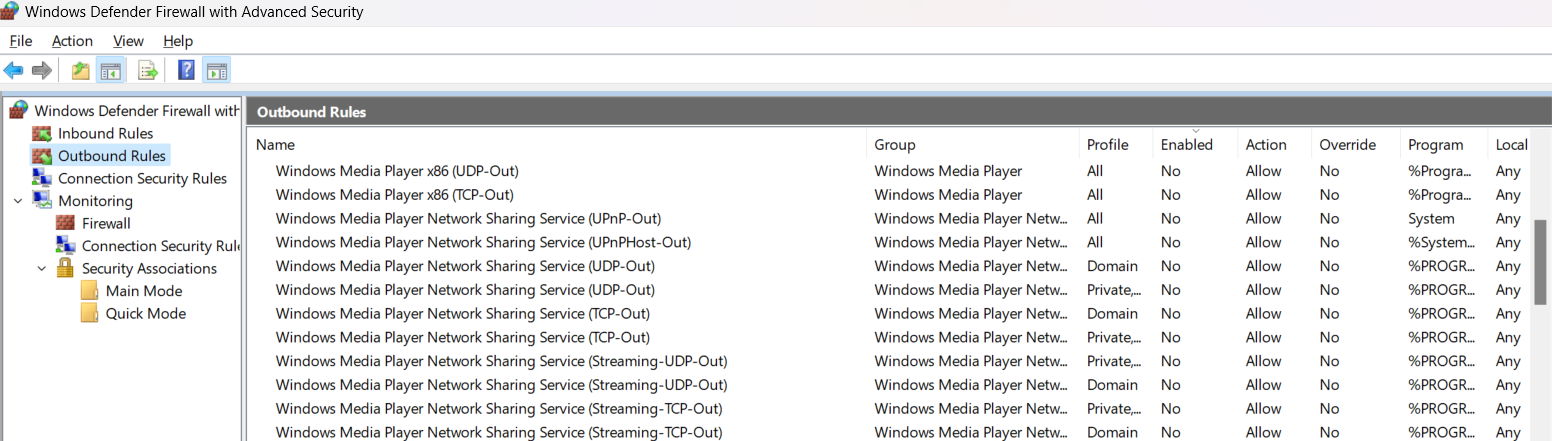
And this is a major breach. If any software can allow itself access to the Internet by adding a rule to the firewall, how can firewall help us and what is the point of firewall at all? Well, not any software can do it. Only the software run as Administrator. Remember another annoying Windows confirmation prompt when running an installer package? This is the point when Windows is shifting liability to the user. Modern software tends to avoid using Admin privileges nowadays. Exactly because of the User Account Control (UAC) guard. Unfortunately, a lot of legacy software is still using installers in elevated mode. And in some cases Admin permissions are really necessary for the program to work.
💡 Outbound connection settings for profile are overridden by specific outbound rules. The rules take precedence.
If a malicious software obtained access to your firewall, disabling VPN is probably the least concern. As for regular software which user installed at will, it sometimes adds firewall rules (and often even confirming that) but never removes.
There are two types of the rules, depending on the action taken: Allow and Block. Luckily, Block actions always have higher priority so even if a program or IP address is explicitly allowed by an Allow rule, another matching Block rule can still override it. And this is what we need: block everything which is not allowed by our own rules.
💡 Block rules have higher priority than Allow rules.
We will be using a Block rule scoped to particular ranges of IP addresses.
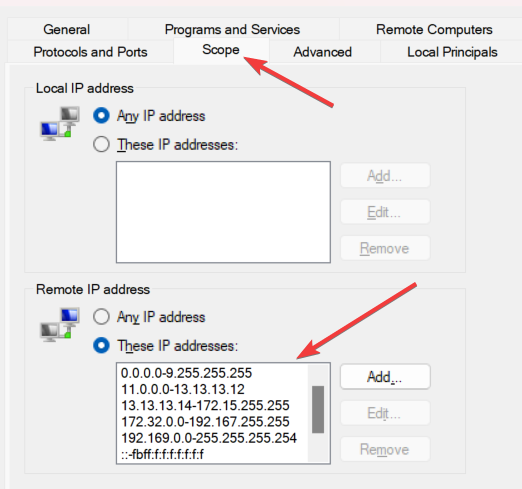
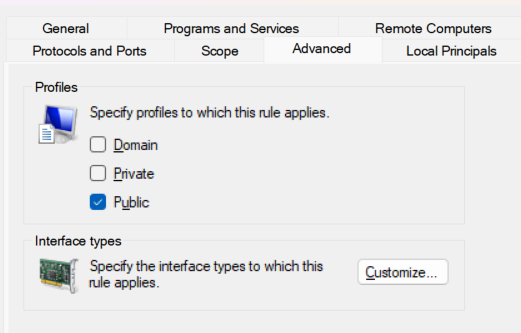
The trick here is not to block some connections which do need to bypass VPN, like LAN traffic and DHCP broadcasts. Because of that we need to exclude some essential IPs. Also, the rule should be applied only to Public networks because we do not want to block Private profile which includes VPN server itself.
IP Ranges to Block
💡 We cannot use Allow rules, only Block. Let’s list exceptions which we want to allow and then reverse them.
✔️ Private IP ranges - access to LAN. Your router must be somewhere in that ranges.
- 10.0.0.0 - 10.255.255.255
- 172.16.0.0 - 172.31.255.255
- 192.168.0.0 - 192.168.255.255
✔️ VPN server itself (several servers)
- 13.13.13.13 (an example)
✔️ IPv4 loopback - for DHCP communication.
- 255.255.255.255
So we have allow list. Now need to convert it to block list.
- 0.0.0.0 - 9.255.255.255
- 11.0.0.0 - 13.13.13.12
- 13.13.13.14 - 172.15.255.255
- 172.32.0.0 - 192.167.255.255
- 192.169.0.0 - 255.255.255.254
Same for IP v6
- FC00::/8 (Every address which starts with FC)
- FD00::/8 (Every address which starts with FD)
- FF00::/8 (Every address which starts with FF)
Again, converting allow list to block list. Note that FC and FD ranges are consecutive.
- :: - FBFF:F:F:F:F:F:F:F
- FE00:: - FEFF:F:F:F:F:F:F:F
✔️ We also need a couple of pre-defined Windows firewall profiles enabled to have network working correctly.
- Core Networking - Dynamic Host Configuration Protocol (DHCP-Out)
- Core Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-Out)`
These rules are defined for all network profiles but this fine because they also define specific port restriction which is DHCP-specific and it has to be open anyway.
Conclusion
Windows firewall is a way to set up VPN kill switch on the OS level. It could be more clear and user-friendly but still it does the job.
⚠️ IP ranges defined in this article are taken from the experience of a single person and checked only on one machine connected to one network. There is a good chance that this configuration is blocking some important services or exposes some unnecessary IPs.